By Callum Golding

When Trinity College South Australia needed to meet Essential Eight Application Control requirements across their entire campus, the challenge seemed insurmountable. Multiple security vendors told them it was too complex, too disruptive, too risky for an active educational environment.
We said it was possible.
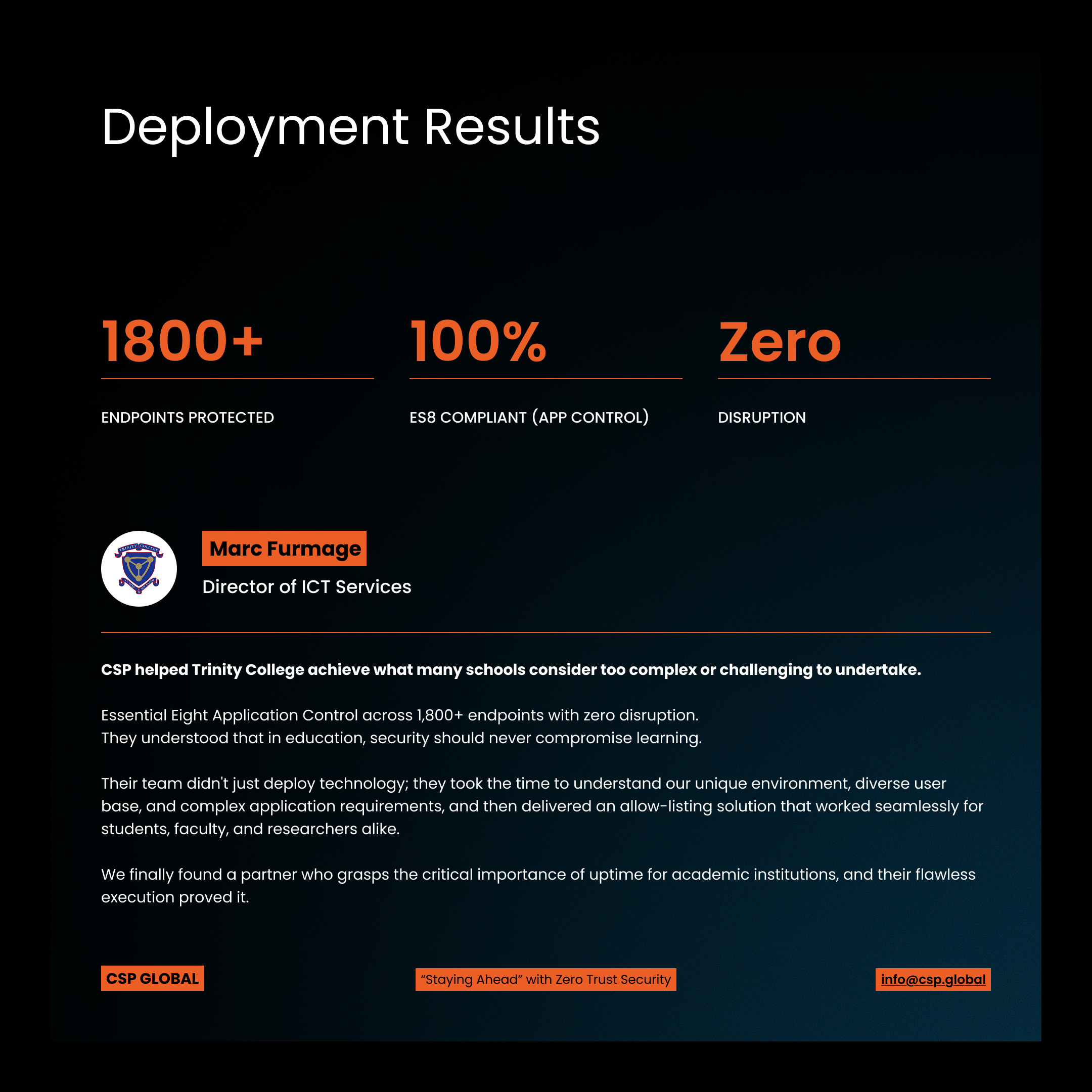
Today, Trinity College operates with 1,800+ endpoints under comprehensive Zero Trust application control—achieving 100% Essential Eight compliance with absolutely zero disruption to teaching, learning, or research operations.
Trinity College faced a uniquely challenging security landscape that many providers simply couldn't navigate:
1,800+ Diverse Endpoints From staff workstations to student devices, research systems to administrative computers—every endpoint required protection without compromising functionality.
Essential Eight Compliance Mandate As an educational institution handling sensitive student and research data, Essential Eight Application Control (Mitigation Strategy One) wasn't optional—it was mandatory.
Dynamic User Environment Unlike corporate environments with standardized software, educational institutions support:
Zero Tolerance for Disruption In education, security cannot compromise learning. A single disrupted lecture, blocked research application, or delayed administrative process is unacceptable.
Many in the Education industry had reached the same conclusion over the years: comprehensive application control was too difficult to implement without significant operational disruption.
Our approach differed fundamentally from traditional security implementations. Rather than deploying technology first and dealing with problems later, we invested deeply in understanding Trinity College's unique environment.
The deployment results exceeded even our expectations:
1,800+ Endpoints Protected Complete coverage across the entire Trinity College campus—from staff workstations to student labs, research facilities to administrative offices.
100% Essential Eight Compliance (Application Control) Full compliance with ACSC Essential Eight Mitigation Strategy One, meeting all requirements for Maturity Level 2 application allowlisting.
Zero Successful Malware Infections Since deployment, not a single endpoint has suffered successful malware infection—a remarkable achievement given the diverse user base and internet-connected environment.
Zero Disruption Not a single blocked legitimate application. Not one disrupted lecture. Not one delayed research project. The deployment was truly transparent to end users.
Maintained Academic Flexibility Despite strict security controls, Trinity College maintained its ability to:
Marc Furmage, Director of ICT Services at Trinity College, captured the essence of our approach:
"CSP helped Trinity College achieve what many schools consider too complex or challenging to undertake. Essential Eight Application Control across 1,800+ endpoints with zero disruption. They understood that in education, security should never compromise learning. Their team didn't just deploy technology; they took the time to understand our unique environment, diverse user base, and complex application requirements, and then delivered an allow-listing solution that worked seamlessly for students, faculty, and researchers alike. We finally found a partner who grasps the critical importance of uptime for academic institutions, and their flawless execution proved it."
Several factors distinguished our implementation:
Deep Understanding We invested time understanding Trinity College's environment before proposing solutions. This discovery phase identified requirements and constraints that other vendors missed entirely.
Educational Expertise Our team understands educational environments' unique challenges. We've implemented security solutions across schools and universities, learning from each deployment.
Flexible Policy Framework Rather than rigid, one-size-fits-all policies, we created flexible frameworks accommodating Trinity College's diverse needs while maintaining security.
Ongoing Partnership Post-deployment support wasn't an afterthought—it was integral to success. We remain actively engaged, adjusting policies as Trinity College's needs evolve.
Trinity College's success provides valuable lessons for other schools and universities considering Essential Eight implementation:
1. Security and Education Can Coexist The perception that robust security compromises educational flexibility is false. Properly implemented controls enhance security without operational disruption.
2. Discovery Drives Success Time invested understanding your environment before deployment pays enormous dividends. Rushing to implementation guarantees problems.
3. Phased Deployment Reduces Risk Gradual rollout with pilot groups identifies issues early, when they're easier to address. Big-bang deployments in complex environments rarely succeed.
4. User Experience Matters Security controls that frustrate users get circumvented. Solutions that work transparently get enthusiastically adopted.
5. Partner Selection Is Critical Choose partners who understand educational environments and demonstrate genuine commitment to your success, not just vendors selling products but partners that will be around to suport you after completion.
If your educational institution faces Essential Eight compliance requirements but worries about operational disruption, Trinity College's success demonstrates what's possible with the right partner and approach.
CSP Global offers complimentary Essential Eight gap assessments for educational institutions, helping you understand your current position and develop a clear roadmap to compliance.
Our educational security services include:

Don't let complexity prevent you from achieving the security your students, faculty, and researchers deserve. Contact CSP Global today to discuss how we can help your institution achieve Essential Eight compliance with zero disruption.
SUBSCRIBE
Copyright © CSP Global 2025. All Rights Reserved.